During a Security Audit from your Windows Server you might have discovered that it is still supporting a Diffie-Hellman primes smaller than 1024-bit which is weak (see https://weakdh.org/) and you wish to change that.
To solve that there are two options possible:
1.) You could disable Diffie-Hellman completely via:
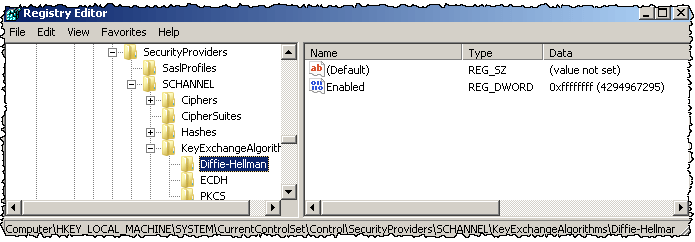
1a.) Run Regedit on the affected server
1b.) navigate to the following Registry location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SChannel\KeyExchangeAlgorithms
1c.) Create a new sub key named Diffie-Hellman (if it didn´t already exists)
1d.) Inside that create a new DWORD called “Enabled” with the value 0
You can also use the following *.reg file:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\Diffie-Hellman] "Enabled"=dword:0
1e.) Reboot the Server
2.) You can upgrade the Diffie-Hellman Prime to 2048bit (or higher if you need) as mentioned by Microsoft here.
2a.) Make sure that you have KB 3174644 installed on the affected server.
2b.) Run Regedit on the affected server
2c.) navigate to the following Registry location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SChannel\KeyExchangeAlgorithms
2d.) Create a new sub key named Diffie-Hellman (if it didn´t already exists)
2e.) Inside that create a new DWORD called “ServerMinKeyBitLength” with the value “00000800” (for 2048 bit)
You can also use the following *.reg file:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\KeyExchangeAlgorithms\Diffie-Hellman] "ServerMinKeyBitLength"=dword:00000800
2f.) Reboot the Server